Warning: Issues with Certbot and Nginx on Ubuntu 20.04
There is currently a bug with Certbot and Nginx on Ubuntu 20.04. It should be resolved in the coming days. https://github.com/certbot/certbot/issues/7951
See comments below for more information.
Prerequisites
You should be using a non-root user with sudo privileges as explained in Ubuntu 20.04 Initial Server Setup.
You should also have Nginx already installed and serving web pages before continuing with this guide. Please see Installing Nginx on Ubuntu 20.04.
Cloudflare Users: Note that you may not need Let’s Encrypt and can instead use Cloudflare’s own shared Universal SSL certificate and an Origin CA. If you want to keep Cloudflare and also use Let’s Encrypt, you must Pause Cloudflare now, otherwise it will interfere with certificate deployment. Once the Let’s Encrypt cert is deployed, you must unpause and set SSL to Full (Strict) in the Cloudflare crypto settings, otherwise you may get a redirect loop error. Be warned that when Let’s Encrypt tries to auto renew after 90 days, it will fail if you have Cloudflare enabled.
1. Install Let’s Encrypt client (Certbot)
Let’s begin by updating the package lists installing Certbot for Nginx on Ubuntu 20.04. Type y and ENTER if prompted.
sudo apt update && sudo apt install certbot python3-certbot-nginx2. Get an SSL Certificate
We will now obtain a cert for our test domain example.com. Certbot has an Nginx plugin for Ubuntu 20.04, which automates the certificate installation.
sudo certbot --nginxEnter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel):Enter an email address where you can be contacted in case of urgent renewal and security notices.
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
-------------------------------------------------------------------------------
(A)gree/(C)ancel:Press a and ENTER to agree to the Terms of Service.
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about EFF and
our work to encrypt the web, protect its users and defend digital rights.
-------------------------------------------------------------------------------
(Y)es/(N)o:Press n and ENTER to not share your email address with EFF.
Which names would you like to activate HTTPS for?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: example.com
2: www.example.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel):If you have multiple domains already configured on your server, you will see a list of them here. In this example, we only have one domain example.com and its www. prefix.
Select option 1 if you don’t want to use the www. prefix in your website address, otherwise select option 2.
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for example.com
Waiting for verification...
Cleaning up challenges
Created an SSL vhost at /etc/nginx/sites-available/example.com-le-ssl.conf
Enabled Nginx socache_shmcb module
Enabled Nginx ssl module
Deploying Certificate to VirtualHost /etc/nginx/sites-available/example.com-le-ssl.conf
Enabling available site: /etc/nginx/sites-available/example.com-le-ssl.conf
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel):Press 2 and ENTER to redirect all traffic to HTTPS.
Redirecting vhost in /etc/nginx/sites-enabled/example.com.conf to ssl vhost in /etc/apache2/sites-available/example.com-le-ssl.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://example.com
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=example.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -You’re done!
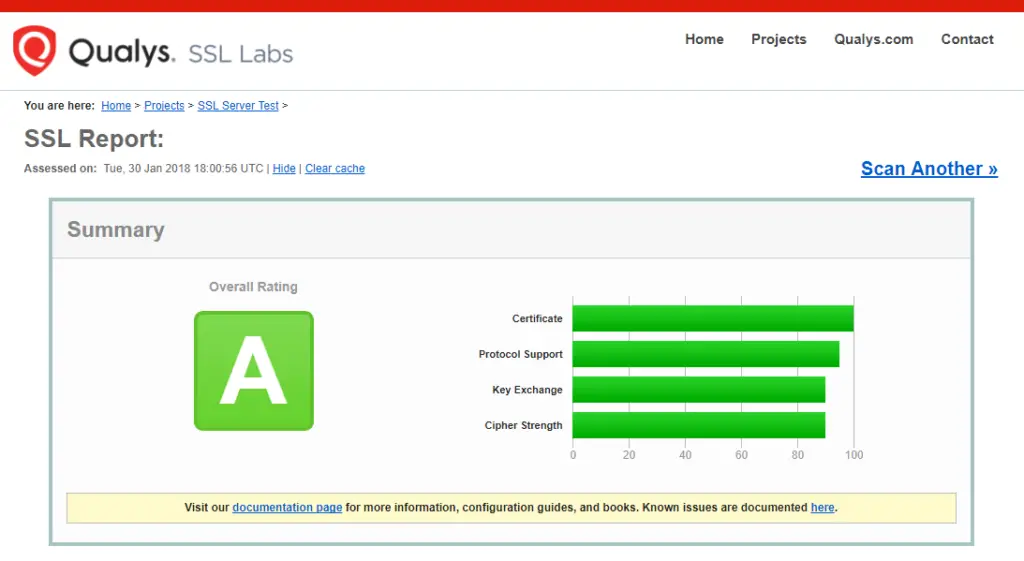
3. Test SSL
You can now go to ssllabs.com/ssltest/ and run an SSL test on your domain.
A successful test should receive an A rating.
4. Auto Renewal
As Let’s Encrypt certs expire after 90 days, they need to be checked for renewal periodically. Certbot will automatically run twice a day and renew any certificate that is within thirty days of expiration.
To test that this renewal process is working correctly, you can run:
sudo certbot renew --dry-runCloudflare Users
Please ensure your Cloudflare SSL settings are correct. Log in to Cloudflare, go to Crypto and make sure SSL is set to Full (Strict). Be warned that when Let’s Encrypt tries to auto renew after 90 days, it will fail if you have Cloudflare enabled.
Let me know if this helped. Follow me on Twitter, Facebook and YouTube, or 🍊 buy me a smoothie.

how to restart system in putty. what is command?
Getting error `Performing the following challenges:
An unexpected error occurred:
AttributeError: module ‘acme.challenges’ has no attribute ‘TLSSNI01’
In /var/log/letsencrypt/letsencrypt.log:
“`020-04-28 02:44:04,207:INFO:certbot.auth_handler:Performing the following challenges:
2020-04-28 02:44:04,208:DEBUG:certbot.log:Exiting abnormally:
Traceback (most recent call last):
File “/usr/bin/certbot”, line 11, in
load_entry_point(‘certbot==0.40.0’, ‘console_scripts’, ‘certbot’)()
File “/usr/lib/python3/dist-packages/certbot/main.py”, line 1382, in main
return config.func(config, plugins)
File “/usr/lib/python3/dist-packages/certbot/main.py”, line 1132, in run
new_lineage = _get_and_save_cert(le_client, config, domains,
File “/usr/lib/python3/dist-packages/certbot/main.py”, line 121, in _get_and_save_cert
lineage = le_client.obtain_and_enroll_certificate(domains, certname)
File “/usr/lib/python3/dist-packages/certbot/client.py”, line 417, in obtain_and_enroll_certificate
cert, chain, key, _ = self.obtain_certificate(domains)
File “/usr/lib/python3/dist-packages/certbot/client.py”, line 348, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
File “/usr/lib/python3/dist-packages/certbot/client.py”, line 396, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, best_effort)
File “/usr/lib/python3/dist-packages/certbot/auth_handler.py”, line 62, in handle_authorizations
achalls = self._choose_challenges(authzrs)
File “/usr/lib/python3/dist-packages/certbot/auth_handler.py”, line 206, in _choose_challenges
self._get_chall_pref(authzr.body.identifier.value),
File “/usr/lib/python3/dist-packages/certbot/auth_handler.py”, line 221, in _get_chall_pref
plugin_pref = self.auth.get_chall_pref(domain)
File “/usr/lib/python3/dist-packages/certbot_nginx/configurator.py”, line 1110, in get_chall_pref
return [challenges.HTTP01, challenges.TLSSNI01]
AttributeError: module ‘acme.challenges’ has no attribute ‘TLSSNI01’
2020-04-28 02:44:04,211:ERROR:certbot.log:An unexpected error occurred:“`
There is a bug with Certbot and Nginx on Ubuntu 20.04. https://github.com/certbot/certbot/issues/7951
Should be fixed soon. In the meantime, you can install using the snapcraft method: https://certbot.eff.org/lets-encrypt/snap-nginx