As well as offering additional security, SSH key authentication can be more convenient than the more traditional password authentication. When used with a program known as an SSH agent such as PuTTY, SSH keys can allow you to connect to a server, or multiple servers, without having to remember or enter your password for each system.
1. Create User with Sudo Privileges
If you already have a non-root account with sudo privileges or if you want to set this up for the root account, you can skip to Step 2. However, it is strongly recommended to use a non-root account for daily administrative tasks to minimize security risks.
Why Avoid Using Root: The root user is the administrative user in a Linux environment with full system access. Using the root account regularly can increase the risk of accidental system changes or security vulnerabilities. Instead, it’s best to create a separate user account with superuser privileges.
Once in terminal, create a new user. In this example we are adding a user called john.
adduser johnGenerate a strong password. You will also be asked to enter contact details, just press ENTER for defaults.
Once the user is created, give it superuser privileges.
usermod -aG sudo johnNow that our new user is set up, we can log out of Linux and return to Windows.
logout2. Download and Install PuTTY
PuTTY is an SSH and telnet client for the Windows platform. You can download from http://www.putty.org
When you install the PuTTY client, it will also install the PuTTYgen utility, which you will use to generate your SSH keys.
3. Generate a Key Pair with PuTTYgen
You can find PuTTYgen in the Start menu. Alternatively, it is located in the installation directory, typically either:
C:\Program Files\PuTTY\puttygen.exeC:\Program Files (x86)\PuTTY\puttygen.exe
Open PuTTYgen, then click Generate and start moving your mouse within the window. PuTTY uses mouse movements to collect randomness, which is critical for generating a secure key pair.
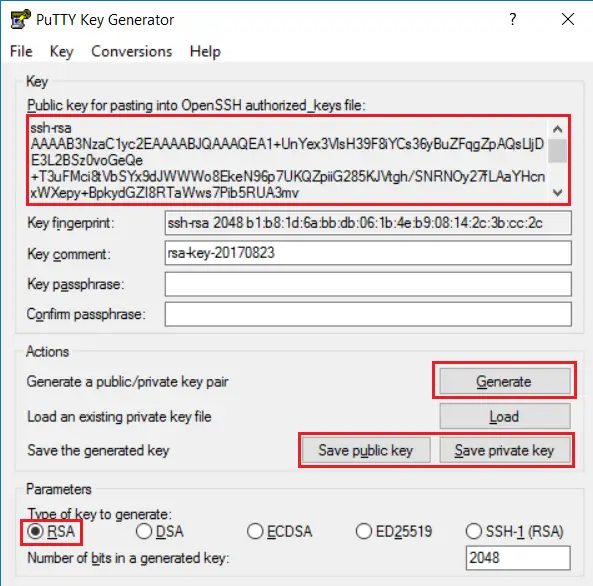
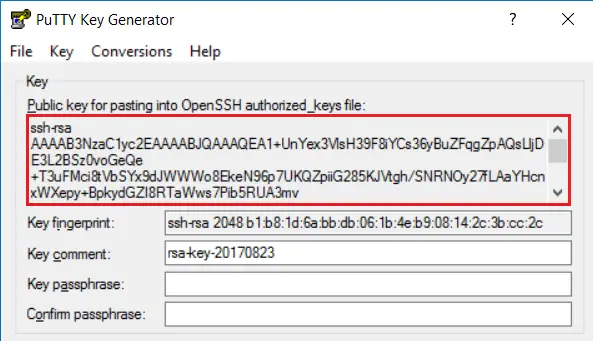
Once the key generation is complete, copy your Public key to the clipboard for later use in terminal configuration. To do this, right-click the key text area, select Select All, then right-click again and choose Copy.
Next, save both your Public and Private keys in a secure location. When saving the Private key, you’ll be prompted to enter a passphrase. While you can leave this blank for easier SSH access without a password, it is recommended to set a passphrase for enhanced security.
Note: If you plan to use this private key to connect over SFTP from your SFTP client, you should export the key in OpenSSH format. To do this, click the Conversions dropdown menu and select Export OpenSSH Key.
4. Install Key on Server
You now need to paste the public key into the authorized_keys file on your server. Log in via SSH using the account you created in Step 1 (or, if you skipped Step 1, log in using your account with sudo privileges or the root account).
Once logged in, create a new directory called .ssh if it doesn’t already exist:
mkdir -p ~/.sshNote that ~/ is shorthand for the currently logged-in user’s home directory, usually located in /home/username/.
Restrict the permissions of the .ssh directory:
chmod 700 ~/.sshNext, use the nano text editor to create or open the authorized_keys file inside this directory:
nano ~/.ssh/authorized_keysnano will open a blank file if it doesn’t exist already. Make sure you have your public key in your clipboard, which you copied from Step 3.
Paste the public key into nano by right-clicking anywhere in the nano program window.
After pasting, you can use the left arrow on your keyboard to move the cursor back and ensure the entire key was pasted correctly.
Save and close the file by pressing CTRL + X, then pressing Y, and finally ENTER to confirm the save.
Now, restrict the permissions of the authorized_keys file:
chmod 600 ~/.ssh/authorized_keysEnsure that the user, and not root, owns both the ~/.ssh directory and the ~/.ssh/authorized_keys file. This command will recursively set the correct ownership. The $(whoami) variable returns the currently logged-in user:
chown -R $(whoami):$(whoami) ~/.ssh/You’re done! If you want to add keys for other users, simply log in as that user and repeat Steps 3 and 4. Or, if you have sudo privileges, you can replace ~/ with the user’s home directory, e.g., /home/username, and replace $(whoami) with their username.
Finally, log out.
logout5. Configure PuTTY Connection
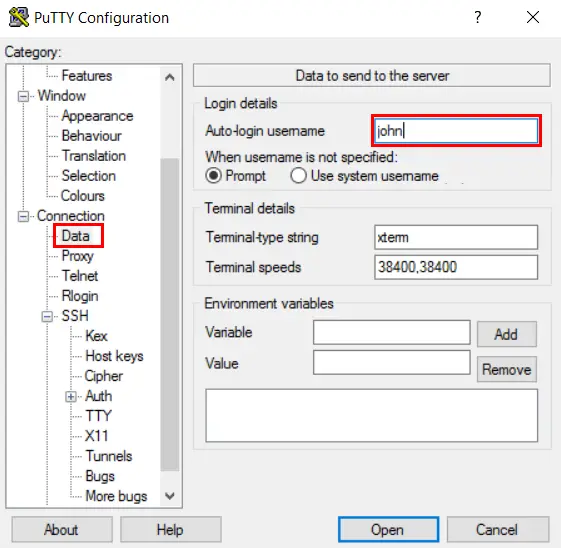
Click Connection > Data in the left-hand navigation pane and enter your username in the Auto-login username field.
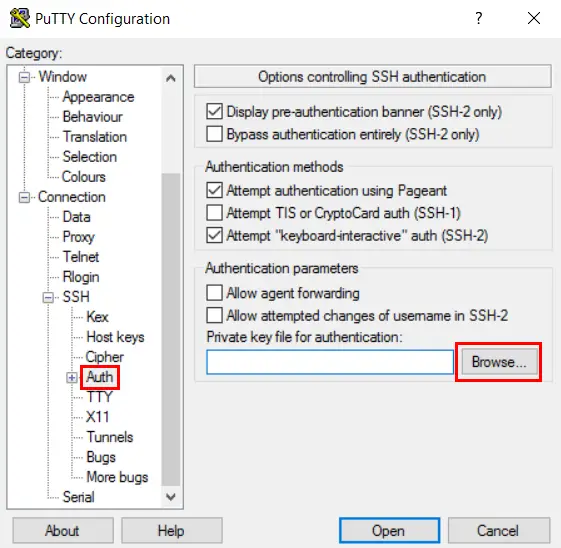
Click Connection > SSH > Auth in the left-hand navigation pane and Browse for the Private key you saved earlier.
Click Session in the left-hand navigation pane and enter your server’s IP address.
Enter a name for your stored session (e.g. “LinuxServer”) and click Save.
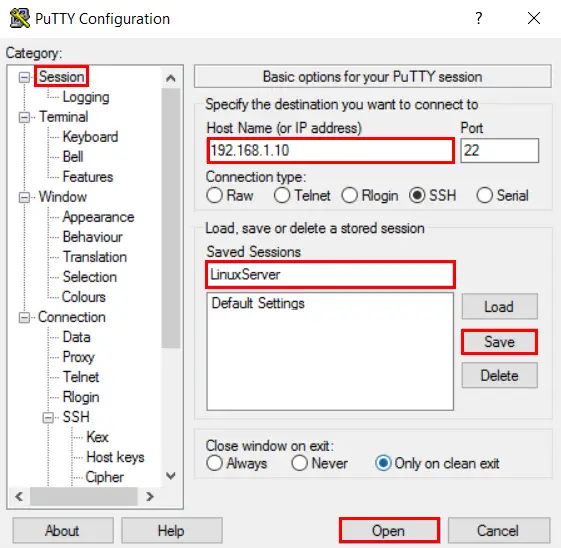
Finally, click Open to connect to your server.
If you saved your key with a passphrase earlier, you will be prompted to enter that passphrase.
Using username "john".
Authenticating with public key "rsa-key-20170825"
Welcome to Ubuntu 24.04 LTS
Last login: Fri Aug 25 08:20:29 2024 from 192.168.1.10
john@linuxserver:~$If you see Authenticating with public key, you have configured SSH key-based authentication correctly. Well done!
Best Practice: Disable Password Authentication
Disabling password authentication is a critical step to further secure your server. With password authentication disabled, only users with valid SSH keys will be able to access the server, significantly reducing the risk of brute-force attacks.
Log in to your remote server with an account that has sudo privileges.
Open the SSH daemon’s configuration file:
sudo nano /etc/ssh/sshd_configPress CTRL + W and search for PasswordAuthentication.
Set the value to no. If the line is commented out, delete the # sign:
PasswordAuthentication noThis will disable the ability to log in through SSH using passwords, ensuring that only SSH keys are accepted for authentication.
Save the file and exit (CTRL + X, then press Y and ENTER).
For the changes to take effect, restart the SSH service:
sudo service ssh restartAfter restarting, your server will only allow SSH key-based logins, providing stronger security against unauthorized access.
Best Practice: Disable Root Login on Your Server
To enhance security, it is recommended to completely disable root login on your server. This ensures that all users log in with their own accounts and use sudo for administrative tasks, reducing the risk of unauthorized access and improving accountability.
Log in to your remote server with an account that has sudo privileges.
Open the SSH daemon’s configuration file:
sudo nano /etc/ssh/sshd_configPress CTRL + W and search for PermitRootLogin.
Set the value to no. If the line is commented out, delete the # sign:
PermitRootLogin noThis will completely disable SSH login for the root account, ensuring that only non-root users with sudo privileges can perform administrative tasks.
Save the file and exit (CTRL + X, then press Y and ENTER).
For the changes to take effect, restart the SSH service:
sudo service ssh restartAfter restarting, root login will be disabled, enhancing the security of your server.
Optional: Disable Sudo Password Prompt or Extend Timeout in Linux
By default, Linux asks for your user password every time you issue a sudo command after a certain inactivity timeout, usually 5 minutes. This behavior is designed to prevent unauthorized commands from being run by someone else or by a malicious script in your absence. While this is the recommended setting for security, you may find it inconvenient if you frequently use sudo.
If you prefer, you can disable the password prompt for the duration of your session or extend the inactivity timeout. Be aware that disabling the password prompt reduces security by allowing sudo access without re-authentication. Extending the timeout slightly reduces this risk while offering more convenience.
For detailed instructions and to understand the implications, see: Disable Sudo Password Prompt or Extend Timeout in Linux
Let me know if this helped. Follow me on Twitter, Facebook and YouTube, or 🍊 buy me a smoothie.

Shoot, I should also note that I followed your reply with the line of code above with a sudo user who is not root.
When I log in it say “Server refused our key”
OK, so I have been scratching my head with this one for a while because I also got that error when going through the guide again.
It turns out the problem is that the ownership of both
/.sshand/.ssh/authorized_keyswas set toroot. You must make sure that the user owns these and not root.This command will recursively set the ownership of the directory. The
$(whoami)variable returns the currently logged in user.sudo chown -R $(whoami):$(whoami) ~/.ssh/More info: https://superuser.com/questions/215504/permissions-on-private-key-in-ssh-folder
Hi, I’ve been stuck on this for awhile now.
Following these steps, I was getting the error of ‘Connection refused’. So, I found elsewhere to created a bridge connection with Ethernet & Wi-fi. Then, using that IP, I was able to get the ‘Using username: ‘ message, along with ‘Server refused our key’, and then asked for a password. The one I created with the original IP didn’t work, I get the message ‘Access denied’.
I’m also UNABLE to connect in this tutorial: https://devanswe.rs/log-linux-windows-using-putty/ using the bridge connection IP – I get ‘Access denied’.
Please help!